Most of us think about the most dangerous computer virus to be one that steals our banking information or wipes our harddrive. While those types of computer viruses and malware (malicious software) are a reality for a huge number of victims, they generally don’t put lives at risk or damage critical government infrastructure. At least, that’s how cyber criminals probably justify it to themselves.
If you don’t have anti-virus software installed on your computer, you’re running the risk of losing all your personal data, banking details being stolen and even being watched without you knowing it. AVG anti-virus offer a free version.
But when it comes to the cyber security of governments, computer viruses and malware allow foreign entities to hack critical infrastructure in targeted cyber warfare.
Critical US Infrastructure Hacked
The most disturbing element of our connected world is the seeming ease of access hackers have to critical infrastructure. In the pre-Internet days, an attack would require physical access to a facility, stake outs, planning, evading detection and a whole lot of weapons and explosions, something akin to a blockbuster Hollywood movie. But not anymore. A cyber soldier in Russia or China can now be sitting comfortably at their desks carrying out the attacks over the Internet on behalf of their governments.
Hackers from Russia have allegedly mounted a successful attack on US water treatment systems by destroying a pump used to pipe water to thousands of homes in Illinois.
The hacker at the center of the attack says “I’ve also seen various people doubt the possibility an attack like this could be done… This required almost no skill and could be reproduced by a two year old with a basic knowledge of Simatic.”
He then goes on to post proof by providing several screenshots:
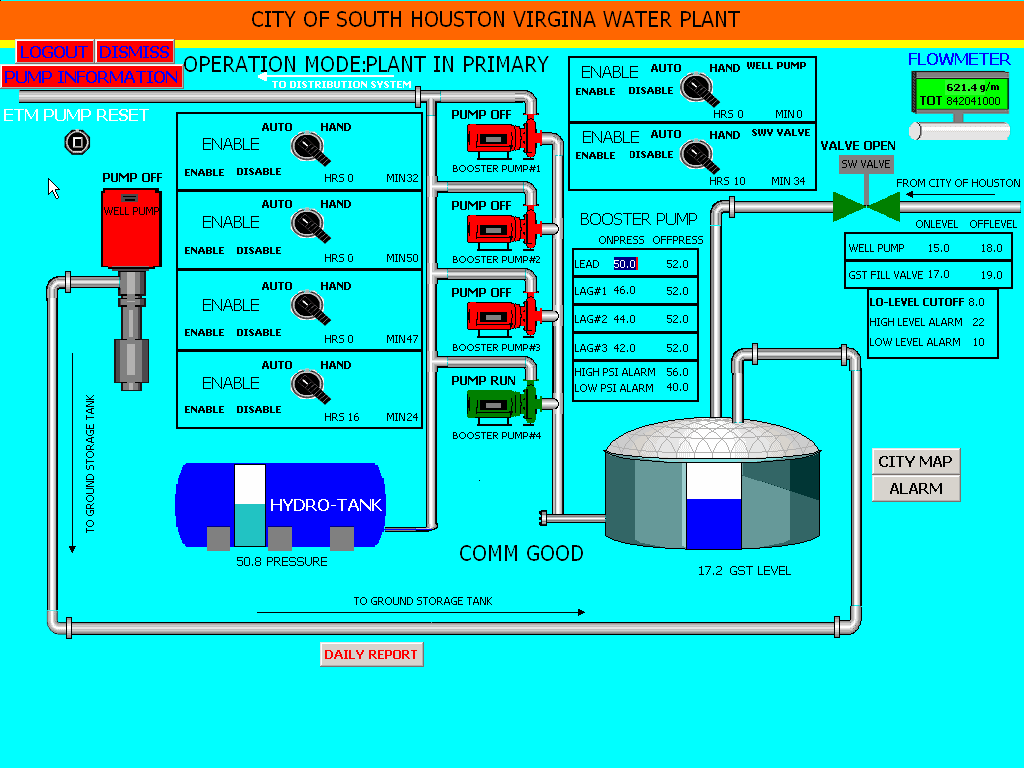
Source
He was able to damage and eventually break the pumps by turning them on and off quickly and frequently.
Just this one incident shows how a hacker from a foreign country can login to critical infrastructure thousands of miles across the globe using stolen usernames and passwords (possibly through the use of a computer virus or malware) and actually control the systems… and take screenshots! I’m guessing that means he had TOTAL access just like he was sitting right there in the control room.
These attacks target what’s known as Supervisory Control And Data Acquisition (SCADA) systems that control equipment used to filter water, mix chemicals, distribute power and route trains and trams.
US investigators Are Very Worried
Similar attacks allegedly coming out of Shanghai, China have also focused on obtaining the ability to manipulate critical US infrastructure. US intelligence officials have admitted to tapping into the activity of the People’s Liberation Army Unit 61398 for years and they have little doubt that an overwhelming percentage of the attacks on US corporations, organizations and government agencies originate in and around Shanghai.
According to Mandiant, a US computer security firm, one cyber target was a company who had remote access to more than 60% of oil and gas pipelines in North America.
“Chinese embassy officials in Washington again insisted their government did not engage in computer hacking, and that such activity was illegal.”
Yet, US government officials have stated that cyber-security, cyber-theft,cyber-intrusions and cyber-threats are brought up in EVERY meeting with Chinese officials. Yes, EVERY meeting. It must be an extremely volatile subject. Watch:
“The United States and China are among the worlds largest cyber actors.”
The US President, Barack Obama, spoke of his concern in the State of the Union address 2013:
The President is sending out a deliberate message warning foreign governments. He calls them “enemies”.
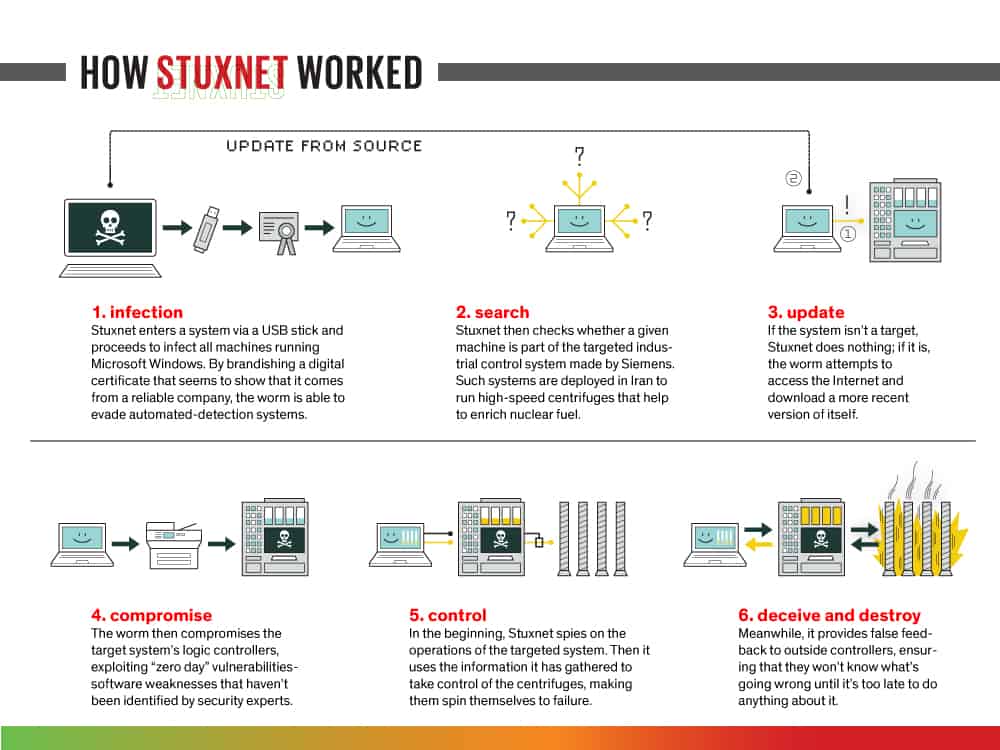
It’s not just a matter of China or Russia attacking the US. The US and other governments engage in cyber warfare too. One of the best known SCADA attacks involved the Stuxnet virus which caused problems for Iran.
Most Dangerous Computer Virus Stuxnet Targets Iran

Source
America and Israel do not want Iran to develop nuclear weapons. In 2006, Gen. James E. Cartwright, who was then head of U.S. Strategic Command, suggested to the George W. Bush administration that cyber warfare could be the best option to damage Iranian centrifuges at its uranium enrichment plant in Natanz. NSA Director, Keith Alexander had the technical know-how to pull it off. The task consisted mainly of gathering intelligence to identify potential targets and create tools to disrupt them.
Without launching a traditional military strike and eager to slow Iran’s efforts toward building an atomic bomb, in 2008 President Obama secretly ordered a cyber-attack against Iran with a cyber-weapon jointly created by US and Israeli experts. The weapon known as Stuxnet could well be the most dangerous computer virus. Stuxnet secretly sabotaged Iranian equipment and was meant to make the Iranians think that their engineers were incapable of running a nuclear enrichment facility. The damage occurred gradually, over months, and Iranian officials initially thought it was the result of incompetence.
The attack caused centrifuges, the fast-spinning machines that enrich uranium, to spin much faster-than-normal until sensitive components began to warp and break. Almost 1,000 out of 6,000 centrifuges were destroyed. Iran replaced the damaged machines and has continued to enrich uranium, saying it’s nuclear program is for peaceful purposes such as generating electricity.
Rafal Rohozinski, a cyber-expert and principal of the SecDev Group, told the Washington Post “This officially signals the beginning of the cyber arms race in practice and not in theory.”
Source
DuQu Cyber Espionage
The virus known as Duqu was apparently built for espionage but shared characteristics with Stuxnet. Although the codes share similar traits, they differ in significant ways. Stuxnet’s payload was designed specifically to disrupt the machines that controlled the speed of centrifuges in a uranium enrichment plant in Iran. Duqu is designed to capture data such as computer keystrokes (i.e. usernames and passwords) and system information.
The new code was written to capture information that can help “mount a future attack on an industrial control facility”, according to cyber security experts at Symantec. “Duqu is essentially the precursor to a future Stuxnet-like attack”.
Flame Computer Malware Virus

Source
The Flame computer virus evaded detection for several years by using a sophisticated program to crack an encryption algorithm and is considered to be among the most sophisticated and subversive pieces of malware ever exposed. Flame was designed to masquerade as a routine Microsoft software update.
Researchers studying the Flame virus suggest that certain characteristics are similar to the most dangerous computer virus Stuxnet and DuQu. Experts described the overlap as “DNA-like evidence that the two sets of malware were parallel projects run by the same entity”.
It uses five encryption methods, three compression techniques and at least five file formats. Its means of gathering intelligence include logging keyboard strokes, activating microphones to record conversations and taking screen shots. It is also the first identified virus that is able to use Bluetooth wireless technology to send and receive commands and data.
Flame only came to public knowledge after Iran detected a series of cyber attacks on its oil industry. The disruption was allegedly directed by Israel in a unilateral operation that apparently caught its American partners off guard.
Future Cyber Security Threats

While governments play politics and cyber war games, it appears the “enemies” can’t just be categorized broadly into “the Chinese” or “the Russians”, but rather, hackers are often solo anarchists outside of government.
The alleged government-funded creation of viruses and malware could very easily fall into the hands of nefarious organizations and ordinary citizens – very smart people who can reverse engineer and re-purpose the virus for their own uses.
Even less organized than the operations of the al-Qaeda terrorist networks, hacker cells may consist of just a handful of individuals across borders not home to any single country. These hackers have most certainly demonstrated the ability and the knowledge to attack critical infrastructure. The biggest concern is when they develop the willpower to co-ordinate a mass targeted attack as an opposition to governments, corporations or other groups.
Victim governments of such events could pin the blame on the country of origin, even if that government was not involved, setting off a chain of attacks and the start of a truly devastating cyber war that impacts lives in the offline world.
Does any of this worry you? Let us know in the comments.
Disclaimer: Links to 3rd party sites included within this article denoted with /go/ in the URL may result in commission being earned if you decide to make a purchase.
Posts related to Most Dangerous Computer Virus Threatens Critical Infrastructure
Website Hacked? 10 Things You Need To Do Right Now How To Create An Unhackable Password You'll Remember
How To Create An Unhackable Password You'll Remember Why Secure Email Is A Myth Worth Busting With A Sledgehammer
Why Secure Email Is A Myth Worth Busting With A Sledgehammer Bitcoin Mining Goldrush Has Begun
Bitcoin Mining Goldrush Has Begun
Tags: computer virusescyber securitycyber warfareduqumalwaremost dangerous computer virusstuxnet




 The Beginners Guide To Blogging
The Beginners Guide To Blogging Image Search Causes Huge Upswing In Website Traffic
Image Search Causes Huge Upswing In Website Traffic Do New Bloggers Need A Small Dose Of Reality?
Do New Bloggers Need A Small Dose Of Reality?


 5 Silly Blogging Mistakes That Can Be Easily Avoided
5 Silly Blogging Mistakes That Can Be Easily Avoided A Social Media Garden Makes Your Website A Happy Home
A Social Media Garden Makes Your Website A Happy Home Do New Bloggers Need A Small Dose Of Reality?
Do New Bloggers Need A Small Dose Of Reality?







 10 Easy Ways How To Get Backlinks To Your Website
10 Easy Ways How To Get Backlinks To Your Website How To Submit Your Website To Search Engines Without The Hassle
How To Submit Your Website To Search Engines Without The Hassle Image Search Causes Huge Upswing In Website Traffic
Image Search Causes Huge Upswing In Website Traffic
